While 2024 had a slight decrease (1%) in the number of data breaches, the impact and scale of these breaches overshadowed the actual number of reported breaches (3,158 for the year). In fact, just six breaches accounted for 85 percent of the total number of notices sent to victims, according to digitaltransactions.net.
These six breaches alone exposed at least 100 million records each. While newsworthy by their sheer scale, massive breaches are a stark reminder that thousands of smaller, less publicized breaches loom every day.
- The average cost of a data breach for a small business is $200,000.
- Retail, tech, and business services were the three most targeted industries.
- According to this report, 94 percent of small and medium-sized businesses were victims of cyberattacks.
Organizations large, small and in between need to take proactive security measures to help mitigate the significant financial and reputational impacts that can follow a breach.
Proactive Security: Get Ahead of Bad Actors
“If the perceived “noise” around cyberattacks has subsided, it is not a sign to become complacent. Data breaches continue each day, though the media may not be highlighting each one.” said Chris Spargen, Associate Director, Solutions Engineering GoAnywhere MFT.
“Take the time to assess the risks that exist to your sensitive or business-critical data and commit to adopting a proactive approach to protect your data as it traverses its life cycles. Every fortress has layers of security, protecting that which is most valuable – we should use this frame of reference when it comes to protecting our data,” he added.
Maintaining the security of your organization’s data is a matter of layering a variety of security measures to create that protective barrier from cyber threats. Here are some key measures to help protect data:
- Encryption: Sensitive data needs strong encryption both while in transit and at rest to ensure if data is intercepted it is unreadable. End-to-end encryption ensures that only specified parties can read the message, even if it is intercepted by encrypting data from the sender’s device to the recipient’s device.
- Secure File Sharing: Solutions such as Managed File Transfer (MFT) that offer secure file sharing, which includes encryption and access controls, are more secure and robust solutions over free consumer methods of file transfer. In addition, secure file sharing includes file integrity monitoring and auditing to stay on top of all file activity. Robust MFT solutions should, ideally, protect files in motion and at rest. However, solutions such as GoAnywhere MFT go above and beyond this benefit to offer a proactive security feature that can stop bad actors before they even enter the MFT environment.
- Access Control: Organizations can limit who can access and act upon data by incorporating role-based access control to limit access only to employees needing that data to do their jobs and by applying the Least Privilege principle, which provides only the minimal level of access to data to do a particular job.
- Cloud Security: If your organization chooses a cloud file transfer service for convenience and familiarity, be sure it is one that offers strong security features including identity and access management, end-to-end security and can comply with industry standards (HIPAA, PCI DSS, GDPR, etc.)
- Disaster Recovery: Having a disaster recovery site and fleshed-out plan can help alleviate risks to data in the event of a data breach or natural disaster disrupting normal operations.
- Employee Education: Regular training around threats and how to better protect the volumes of data exchanged each day can go a long way in protecting data entrusted to your organization.
- Zero Trust Security Architecture: This approach assumes that all external and internal networks are not to be trusted and continually verifies users and devices and puts limits on access based on user role and location.
By combining multiple layers of security, organizations can significantly improve their ability to protect sensitive data and files from threats, making it much harder for attackers to succeed.
Easy Accessibility Can Cause Chaos
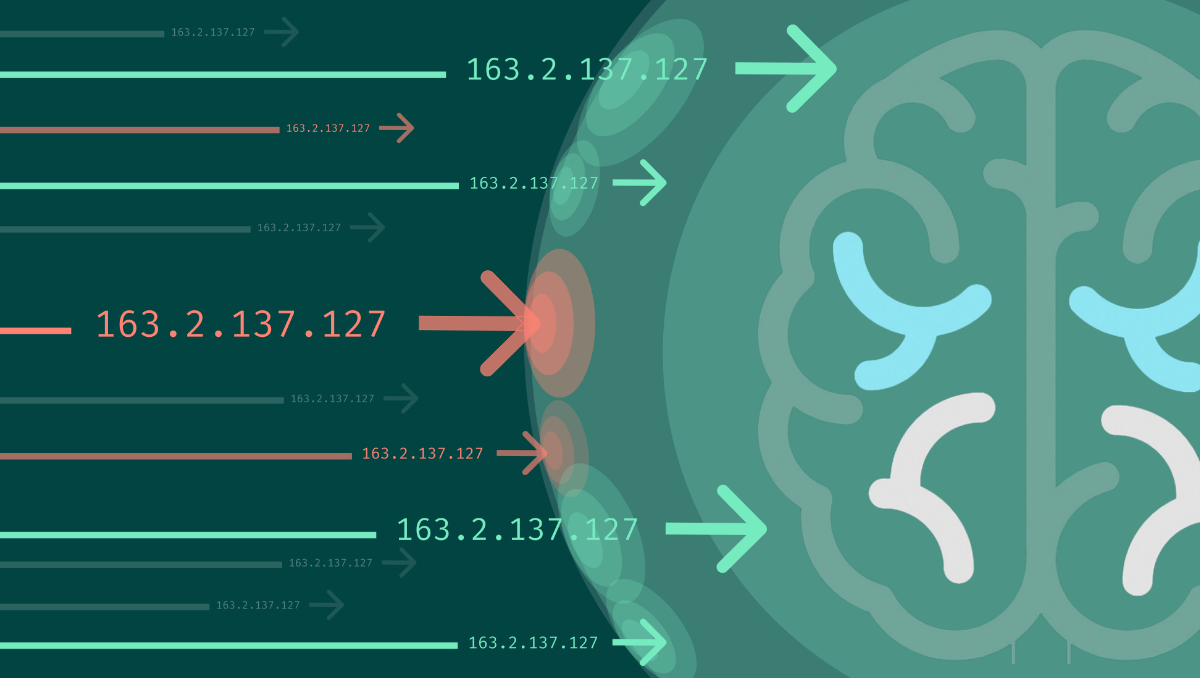
“Bots are often deployed to sniff the web and find vulnerable servers, reporting back to their command center with information about servers that pose opportunity. These bots contain IP addresses, often referred to as a key IoC, or Indicators of Compromise”, noted Spargen. “If you can keep bad actors from entering your environment in the first place, you can go a long way in preventing cyberthreats.”
Common cyber-attacks where patterns of IoCs such as IP addresses are used include:
- Distributed Denial of Service (DDoS)Attacks: These attacks are often carried out to take down servers. Traffic from bad or compromised IP addresses can exhaust a server’s available connections, causing sites and services to be down for hours or days.
- Brute-force Attacks: Bad IP addresses are often associated with brute force login attempts on servers to gain unauthorized access to systems and potentially breach or exploit data.
- Malware Distribution: Exploiting Vulnerabilities: A client with an IP can upload malware to a server if the server has a weakness—like an unpatched web application or a file upload feature with poor validation. For example, an attacker could use a client device to send a malicious file (say, a PHP script disguised as an image) to a server via a vulnerable upload form. Once there, the malware executes and compromises the server. The client’s IP is the source of that upload.
GoAnywhere MFT Offers Proactive Security and Stops Bad IP Addresses
If your organization uses MFT for file transfers, note that GoAnywhere MFT is the only MFT solution that offers a feature which identifies and puts the brakes on those bad IP addresses by leveraging the dynamic intelligence database of Threat Brain from Fortra.
“Legacy MFT application security is reactive, alerting to danger only after a system has been attacked,” added Spargen. “Unfortunately, this leaves plenty of time for brute force, DDoS, and other attacks to exploit vulnerabilities, replicate them across systems, and lead to widespread attacks, even Zero-Day incidents. It’s common for an attacker to make dozens of attempts before they trigger reactive monitoring tools, like Brute Force or DDoS monitoring, to alert an administrator.
“With a simple activation, GoAnywhere can stop bad actors using poor or suspicious IPs from entering your environment, adding another layer of security for protecting your sensitive data,” he added. “This novel feature in the MFT space gives our customers a proactive approach and lowers the chances of bad actors carrying out attacks. Fortra’s unique Threat Intelligence provides GoAnywhere MFT with a security awareness that can’t be matched.”
Proactive Security Gets a Boost from GoAnywhere and Threat Brain
No other MFT solution can stop bad actors from entering your MFT environment like GoAnywhere with the power of Threat Brain. Request a demo for all of GoAnywhere MFT’s security features today.
