Many organizations have an SFTP server installed where their trading partners can connect to securely upload and download sensitive files.
SFTP Server in the DMZ
Traditionally SFTP Servers have been installed in the DMZ (or public facing) segment of the network since organizations were fearful of opening inbound ports into the Private (internal) network.
Keeping the SFTP Server in the DMZ, however, has posed several problems. The primary issue is that files have to be stored in the DMZ when they are dropped off by partners, or otherwise staged temporarily for pickup. Those staged files have a higher risk of being accessed by hackers since the DMZ is more exposed to the Internet. You could require those staged files to be encrypted with something like Open PGP, but many auditors don't like to see any sensitive files in the DMZ, encrypted or not. Another issue is that you often have to write scripts to copy the files back and forth between the DMZ and private network, which takes programmer effort and can lead to errors.
SFTP Server in the Private Network
To keep sensitive files out of the DMZ, some organizations have moved their SFTP server into the private network.
This approach eliminates the need to write scripts for moving files back and forth. The big downfall of this approach is that ports were traditionally opened into the private network for trading partners to gain access to the SFTP server. These open ports could create a potential risk for attackers to gain access to the private network. In today's security-conscious environment, most IT auditors do not like to see any inbound ports opened into the private network... especially if you are storing sensitive PCI DSS or HIPAA data on those servers.
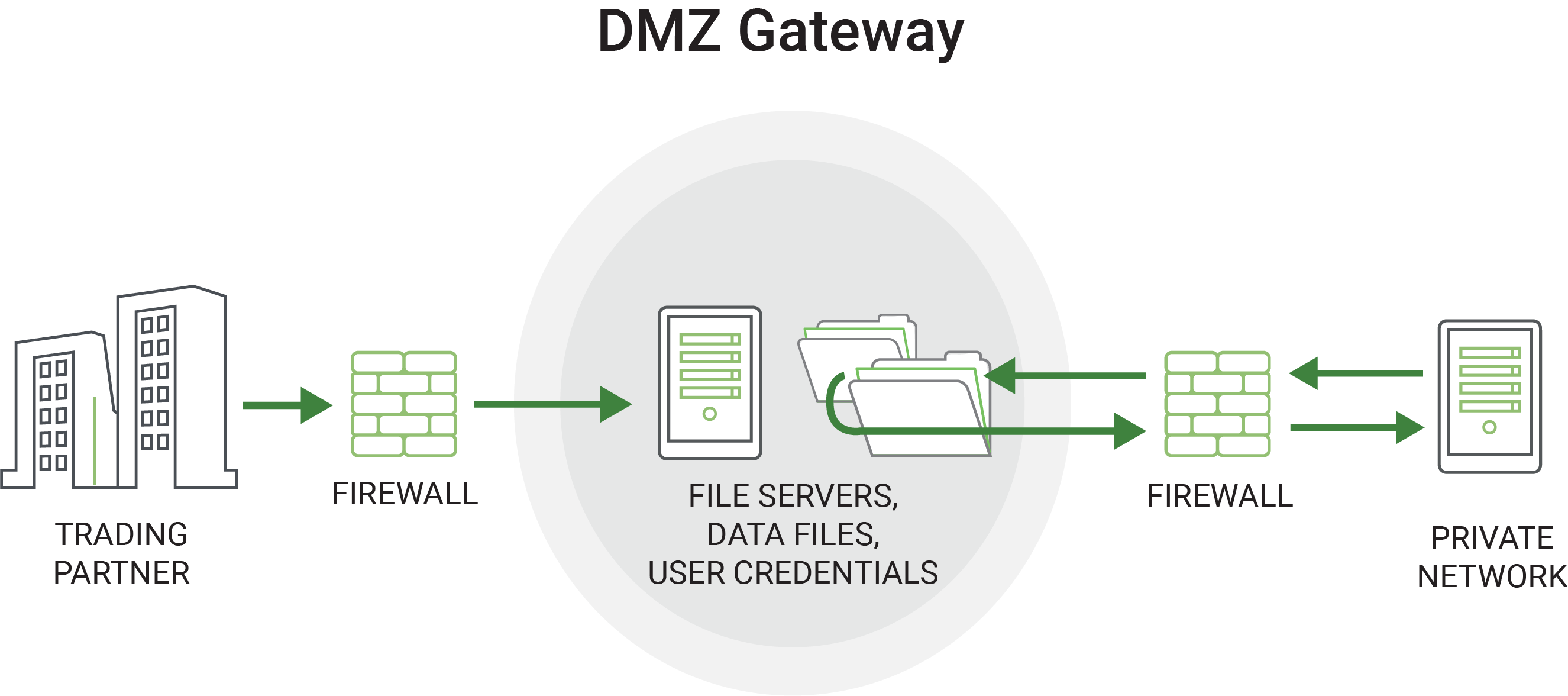
Gateway in the DMZ while keeping the SFTP Server in the Private Network
An approach that is quickly gaining in popularity is to implement a gateway component in the DMZ. The gateway will serve as an enhanced reverse proxy which does not require inbound ports into the private network.
At startup time, the SFTP server will establish a special control channel with the gateway, which is kept alive continuously. When partners connect to the gateway, it will make requests over the existing control channel to the SFTP server. The SFTP server will then open any data channels needed back through the gateway to service the trading partners. The whole process is transparent to the trading partners. No data is ever stored in the DMZ since it is simply streamed through the gateway.
Related Reading: What is a DMZ Server?
A gateway in the DMZ therefore solves two major security issues:
- No files need to be stored in the DMZ, including user credentials
- No inbound ports need to be opened into the Private network
Since a proprietary control channel is used to communicate between the gateway and the SFTP server, you will need to purchase both components from a single vendor. When looking for the right gateway for your organization, make sure it is easy to set up and manage. It is critical that it does not require inbound ports into the private network or require any data to be stored in the DMZ.
Learn More About DMZ Secure Gateways
Want to learn more about DMZ Secure Gateways? View this informative whitepaper: DMZ Secure Gateways: Secret Weapons for Data Security.
