What is Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service (RaaS) is a new pay-for-use business model used by ransomware developers where malicious actors (known as affiliates) can outsource or lease already-developed ransomware attacks the same way legitimate software developers lease Software-as-a-Service (SaaS) products.
Because RaaS is a subscription-based model and all it takes is signing up for the service, even those without advanced technical knowledge can take advantage of the ransomware variants. RaaS users don’t need to be particularly skilled or even experienced to proficiently use the tool, therefore RaaS solutions can unfortunately empower even the most novel of hackers to execute a highly sophisticated cyberattack.
RaaS outlets are relatively easy to find on the dark web and are advertised in the same way goods are advertised on the legitimate web. A RaaS kit may include 24/7 support, bundled offers, user reviews, forums, and other features identical to those offered by legitimate SaaS providers.
Related Reading: The Evolution of Ransomware Infographic
Ransomware vs. RaaS
What is Ransomware?
Before diving further into RaaS, let’s start by defining its base. Ransomware serves as a type of malware that typically encrypts files on an organization’s computers and servers. The attack will then export sensitive data and hold it hostage, imprisoning the targeted files and making decryption practically impossible without a decryption key.
Once the systems have been encrypted, a ransom is then demanded – usually in the form of cryptocurrency – in exchange for the decryption key and to keep the confidential files from being released or sold to fellow malicious actors on the dark web.
Ransomware attacks are largely opportunistic and typically infect a myriad of easy targets in the hopes of collecting a high financial reward. Unless organizations have a contingency plan in place to recover the stolen data or the encrypted files lack value, the victims will often end up paying the ransom or lose their files altogether. According to PurpleSec, the average ransom paid in 2021 increased by 82 percent year-over-year to $570,000, while the average total cost of recovery from a ransomware attack according to Sophos is now nearly $2 million.
It’s worth noting that even if the victims pay the ransom, they still may not regain access to their data. As for whether a victim should pay the ransom or not, the FBI recommends against it and the U.S. Treasury Department is even exploring financial penalties levied by the Office of Foreign Assets Control (OFAC) to organizations who pay a ransom to recover data.
Related Reading: Ransomware Attacks on Small Businesses: How to Mitigate
Ransomware vs. RaaS
Like ransomware itself, RaaS is a criminal exercise and is almost always illegal anywhere around the world. However, with RaaS, ransomware is no longer limited to the developers who create it as they can now sell their product to ransomware affiliates who intend to use it to extort organizations.
Ransomware is something that RaaS operators provide as a service. A single threat actor can develop their own ransomware code, but it is limited in reach. RaaS expands the accessibility, potential reach, and overall, the entire ransomware threat landscape. Instead of a single group using ransomware code to attack victims, many groups of attackers can use RaaS to exploit victims with a ransomware infection.
RaaS also reduces the cost to perform attacks for affiliates since prebuilt ransomware is utilized and ransomware kits can be purchased for prices as low as $175. However, for ransomware developers, RaaS is profitable as affiliates owe cybercriminals a percentage of the paid ransom.
Related Reading: The Biggest Cyber Risks Organizations Face Today
How Does the RaaS Model Work?
For the RaaS model to find success, malicious actors work with reputable RaaS developers who are skilled in creating expertly coded ransomware with a high chance of penetration success and a low chance of discovery.
Once the ransomware is developed, it’s then modified to a multi-end user infrastructure and is then ready to be licensed to potential affiliates. The revenue model for RaaS solutions mirror legitimate SaaS products as affiliates can either sign up with a one-time fee or a monthly subscription.
RaaS itself is a business and it’s a big one at that, in fact, total ransomware revenues in 2020 were around $20 billion.
Some of the most well-known RaaS providers are DarkSide, Dharma, LockBit, Maze, REvil, and Ryuk. However, there are many others and RaaS operators regularly disappear, reorganize, and re-emerge with newer and better ransomware variants.
Check it Out: StateScoop's Ransomware Map Featuring Attacks on Government Entities
How Do RaaS Attacks Work?
Most ransomware attacks are breached through phishing attacks. This is a method of stealing sensitive data through a seemingly innocuous source such as by clicking on a link within an email that appears legitimate, but rather is malicious. RaaS affiliates present victims with very convincing phishing emails and when a link is clicked the ransomware is clandestinely downloaded.
Since the beginning of the Coronavirus, COVID-19 themed phishing emails have been flooding inboxes and are often found to be very convincing, especially to someone who may be panic-stricken.
Related Reading: 7 Steps to Protect Yourself Against Corporate Spear Phishing
Related Reading: How the Coronavirus is Impacting Your Data Security
Step-By-Step Example
Here is a step-by-step example of how a RaaS attack may occur according to Current Ransomware Threats:
- The ransomware developer creates a custom attack (exploit code) that is then licensed to a ransomware affiliate for a fee or for a share in proceeds from the attack.
- The affiliate updates the hosting site with the custom exploit code.
- The affiliate identifies and targets an infection vector and delivers the exploit code to the victim (e.g., via phishing).
- The victim clicks the link or goes to the website.
- The ransomware is downloaded and executed on the victim's computer.
- The ransomware encrypts the victim's files, identifies additional targets on the network, modifies system configurations to establish persistence, disrupts or destroys data backups, and covers its tracks.
- The victim receives a ransom note and is instructed to pay ransom with untraceable funds, typically cryptocurrency.
- A money launderer will move the money through multiple transformations to obscure the identities of the ransomware affiliate and developer.
- The ransomware affiliate may send a decryptor to the victim once a ransom payment has been received. Or the affiliate may make additional demands on the victim or do nothing at all, leaving the victim with encrypted files.
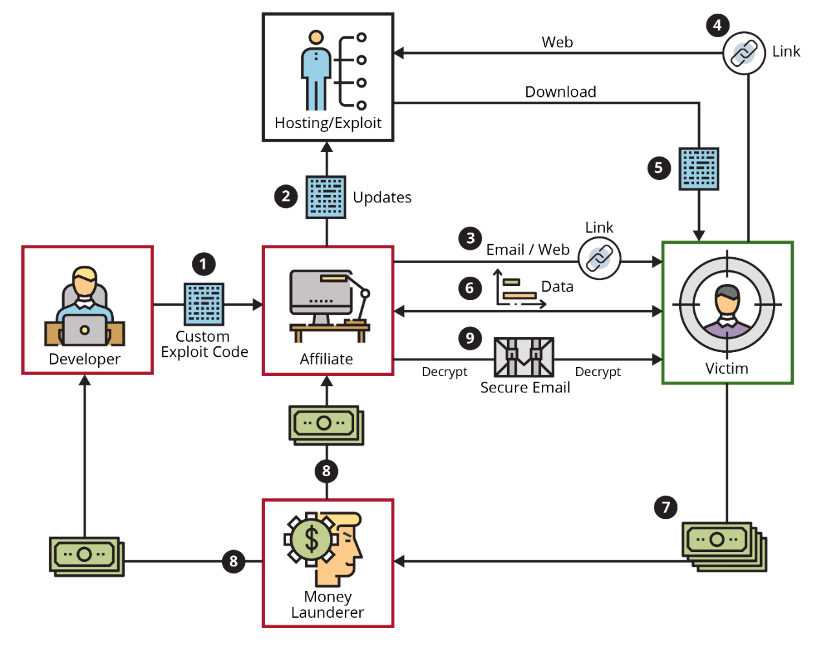
Source: An Updated Framework of Defenses Against Ransomware - Software Engineering Institute at Carnegie Mellon University
Preventing RaaS Attacks
Recovering from a ransomware attack is not only difficult, but it's obviously costly with the largest ransom demanded so far in 2021 listed at $100 million. Therefore, it’s best to prevent them entirely from happening in the first place.
The steps to prevent a RaaS attack are the same as preventing any ransomware attack, as RaaS is just ransomware packaged for ease of use by anyone with ill intent.
The Steps
- Understand your risks. Rather than assume your organization won’t be attacked or that your cybersecurity program is effective, assume that it isn’t. Understand your greatest weaknesses and vulnerabilities, identify risks and cracks in your cybersecurity defenses, and take proactive steps to monitor your network.
- Ensure data backup and recovery. The first and arguably most critical step is to have a data backup and recovery plan in place. Ransomware encrypts data, rendering it inaccessible to users. Don’t solely rely on cloud storage, backup data on external hard drives too. If an organization has up-to-date backups that can be used in a recovery operation, the effect of an attacker encrypting data can be reduced. If a backup is not performed regularly, a ransomware attack could have dire consequences.
- Update software. Ransomware often exploits known vulnerabilities in applications and operating systems. Updating software as patches and updates come out is necessary to help prevent ransomware attacks.
- Update (or establish) your cybersecurity program. Your organization’s cybersecurity program is the full set of your security policies, procedures, and standards and is built to protect your business and respond effectively when needed. Take the time to review your policy and ensure that it’s still applicable for your specific needs and takes any new or updated data security compliance requirements into account. No matter how complex your system is, make sure your cybersecurity policy can easily keep up with changes to your organization, system setups, and other policies.
- Build a culture of security. Data Security is only as solid as the various elements that support it. Layering robust, proven solutions to ensure your sensitive data remains secure from start to finish is a proactive approach.
- Invest in user training. Take the time to educate your employees – informed employees are the number one stopgap for your organization’s data security.
- Use antivirus and anti-malware solutions. Ensuring you have an antivirus and anti-malware application(s) installed can make a big difference in whether your organization is a cybersecurity cautionary tale or a cybersecurity pro.
- Implement advanced anti-phishing protection. A common attack vector for ransomware is email phishing. Having some form of anti-phishing email security in place can potentially help prevent RaaS attacks.
- Ensure data is secure at all points in its lifecycle. Assign appropriate access, ensure sensitive data can’t leave its borders, and verify that data is secure both at rest and in transit with the help of a managed file transfer solution.
Related Reading: Data Security Best Practices Every CISO Should Know
Keep Data Secure with GoAnywhere MFT
A robust managed file transfer solution, like GoAnywhere Managed File Transfer (MFT) isn’t just for sending files securely between users and systems. It comes with many features and modules that can be used to streamline and automate processes, track file transfer activity, and more.
With GoAnywhere MFT by your side you can improve security, simplify file transfers, and meet compliance requirements all while keeping your sensitive data better protected against potential RaaS attacks.
Related Reading: How MFT Fits into Your Data Security Suite
