
Heists of yore claimed stacks of cash, gold bars, or even dazzling jewelry as their prizes. Today, data is the motherlode for criminals. And rather than enormous vaults and security guards, organizations now employ data security software to keep their data protected.
Digital data requires different types of protection than locks and keys. And unlike physical goods, data typically needs to move freely between customers, organizations, and trading partners. The inherent need for data movement introduces both complexities and vulnerabilities into processes for many organizations.
Keep reading to discover each stage of the data security lifecycle, and how you can achieve end-to-end encryption and protection for your data.
What is a Security Lifecycle?
At a high level, the security lifecycle is a schema that helps IT teams understand what information and systems need protection, and how information flows through the business from intake to deletion.
What is the Purpose of the Data Security Lifecycle?
The short answer is: gaining visibility. In fact, CISOs agree that data visibility is the biggest cybersecurity weakness, according to a recent Fortra study.
Knowing what data you have on hand, where it is, and how it is being used are among the first steps towards better overall data security, especially with the massive amount of data generated, collected, and transferred every. Single. Day.
The data security lifecycle (also known as the lifecycle of data), functions as a blueprint to help organizations identify where their data is vulnerable, and where gaps could lead to data breach.
Related Reading: What is Data Security?
What are the Phases in a Data Security Lifecycle?
The data security lifecycle is made up of seven unique stages:
- Capture*
- Store*
- Analyze
- Use
- Publish
- Archive
- Purge
*Some information management lifecycle designs do not include the capture and storage steps, but these establish the foundation for the data’s full term at your organization. Considering security during these stages is essential to start on the right foot.
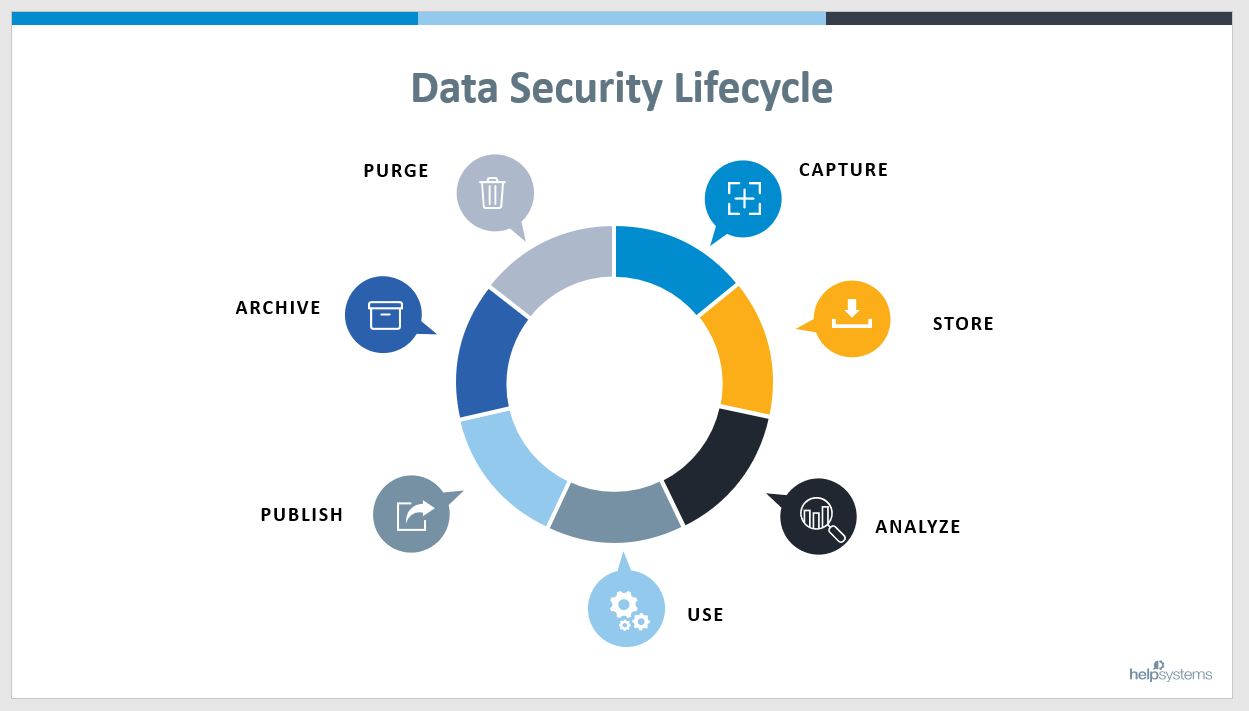
As a cycle, these stages repeat, overlap, and backtrack. While “lifecycle” may capture the process from a high level, the actual flow of data is more fluid, especially as data is processed, updated, and reclassified. Your organization’s processes may skip stages entirely, or repeat certain stages multiple times before they move onto the next.
How to Address the Data Security Lifecycle in the Cloud
Cloud computing comes with its own benefits and challenges. Although data is inherently more exposed in the cloud (since it no longer lives exclusively within your organization’s four walls) cloud data security is strong. Robust security features are typically built into cloud-based solutions and are updated frequently.
When it comes to the data security lifecycle, the stages are the same in the cloud as on-premises. The cloud may, however, offer more flexibility in shoring up data protections, since it’s much more scalable than physical machines in your server room.
Related Reading: SFTP and the Cloud: How to Transfer Your Data Securely
End-to-End Encryption: Achieving Data Security at All Stages of the Lifecycle
1. Data Capture
Also often called data intake or data collection, this stage is when data is introduced to your organization’s internal systems. As the origin of data within your organization, it’s best to set yourself up for success. One part of this is a streamlined data intake process, but it’s also important to gatekeep what types of information are you are collecting and storing, and to guard against malicious files.
Email is ubiquitous across everyone’s personal and professional lives. That level of access, however, has made email a popular vehicle for would-be hackers and phishers. With $18.9 billion in annual fraud loss attributed to advanced phishing attacks, it’s important to ensure that only legitimate emails – and the data contained therein – are making their way into your organization. With email security tools, you can gain the ability to detect, defend against, and deter phishing, compromised business emails, and other advanced types of email attacks.
Threats aren’t only arriving via email. They can also make their way to your organization through the web and solutions you or your trading partners use. Threat protection solutions can take the risk out of both opening the files you receive and everyday web usage by inspecting to detect and sanitize any embedded malware threats. And they do so without pausing your work thanks to real-time inspection and automated removal of only the malicious code.
Related Reading: The Top 10 Cybersecurity Threats of 2021
It’s also important to keep in mind that you should only collect sensitive data with a business problem in mind. This helps you have less sensitive data on hand and meet data privacy requirements and regulations.
2. Data Storage
A secure storage service – whether on-premises or in the cloud – that offers detailed user access roles is the best place to store your data.
In terms of user access, the best practice is to start at the least amount of access possible and grant access only as needed. For example, for specific business purposes or only within a limited timeframe. Using minimal rights as the default ensures that nosy employees do not inadvertent breach data they should not view, or that, in the case of a successful phishing attempt, a hacker can only view limited data.
3. Data Analysis
The basis of data security is: what needs protecting, and why?
Not all data is equal, and some needs more extensive protection. Says Steph Charbonneau, Senior Director of Product Strategy and Data Security at Fortra, “You need to know what the data is. Once you know what the data is, you can start minding the gap for the sensitive, private personal data regulatory bodies worry about, and how to trigger those things to help users along.”
The first order of business is identifying and classifying your data. While users can do this manually, there are tools for exactly this type of work. Data Classification solutions label and sort your data, then automatically applies pre-set security levels to ensure appropriate user access and control over data.
With either this type of process or solution in place, you can easily identify and sort the most sensitive and confidential data from the more mundane and shareable, without the need for more nuanced layers of security for data exchanges and transfers.
4 & 5. Data Usage & Publishing
Usage refers to when data is used and moved internally at your organization, and publication can refer to both sharing with external stakeholder and when the data is made available for public consumption, for example, as stats in a presentation or white paper. These two types of data sharing run similar risks: the transfer itself, unwanted eyes, or inadvertent data sharing.
Ensure that the data you’re trying to share is appropriate for outside eyes with an Advanced Data Loss Prevention (DLP) solution. It’s easy to simply send along the file that a colleague or trading partner requested, but it could contain sensitive information you’re not aware of, like file metadata, or even text contained in an image. DLP can redact sensitive text, even in scanned images and images, as well as sanitize your documents by removing metadata from documents, including track changes, author information, and more.
Once you’ve ensured your data is identified and classified, cleared of any potentially sensitive data, and approved for sending, it’s time to securely transfer the files. One of the most robust methods of secure file transfer is managed file transfer (MFT). MFT protects your data when it is most vulnerable by encrypting it in transit. That way, you can be confident that only the intended recipient can access the file, and that they receive the data unadulterated.
Related Reading: How MFT Fits into Your Data Security Suite
6 & 7. Archive & Purge Data
According to most data privacy policies, including the GDPR and HIPAA, data should only be retained for as long as it is required. Even if it’s no longer of use to your organization, old data is still a tempting target for hackers.
When to Archive and When to Delete
Some industries are required to keep data on hand for a set period of time, whether or not they are actively using it. In these cases, it’s important to have secure archiving processes in place, along with tracking and a plan for the eventual destruction date. Moving data to an archive also keeps it further from active users, and, with user access roles, you help limit accessibility and reduce risk even more.
All data is risky, and when you no longer need it, you should delete it. The less data you have on hand, the more you lower your security risk. To assist with the proper protocols, NIST has recommendations in place for how to handle data deletion and destruction based on sensitivity.
Your Data Security is Only as Strong as Your Processes
While the information lifecycle helps IT management at a high level, it’s important to know that your data is only as secure as the actual processes you have in place. When you layer robust security solutions, you’re taking steps to ensure that your data is protected from start to finish. With Fortra’ suite of data security solutions, you can fill any existing gaps in your organization’s data protection needs, improve upon your existing processes, and ultimately strengthen your data security from end to end.
